lets just say something changed on tailscale surrounding webfinger that was no longer allowing me to access the tailscale admin console. not sure why, tech support for tailscale (which is great btw) confirmed the issue. so here it is. don’t love github, google or the other Oauth options, and with the OIDC not functioning i decided to forge on with headscale. one thing i will say is this solution was confounding. some spotty instructions and alot of diggin around the net to get the right things in place.
start with the proxmox lxc template in community repos for headscale, it works fine. here’s a link if you havent been there before:
https://community-scripts.github.io/ProxmoxVE/scripts?id=headscale
follow installer directions and imho the admin console is unnecessary, to get things working i had to do 99% of the work through the CLI. so first off, and i may be making some assumptions here on the best ways to achieve them, my goals here are:
- install headscale on proxmox lxc, and get it functional > wanting it to work like i had with tailscale.
- build an exit route and route traffic through my home network > for many complicated reasons, but one is access to all proxmox IP’s and my home network LAN without running tailscale on each device and from anywhere in the world.
- be able to connect my laptop and phone remotely > this was the complicated part and im still not sure how i achieved it ;}
https://headscale.net/stable/usage/getting-started
so headscale install was pretty straight forward. what was not was setting up the user, when/why key were needed and howto designate an exit route and routes. also not super obvious, so i did what i always have done, is compartmentalize the tailscale end of it…i.e. the exit route, routing needs for my server to was installed on a additional lxc with tailscale installed as a client on the same proxmox server.
so on the headscale install side. once installed i had some quick commands:
systemctl enable headscale
systemctl start headscale
headscale apikeys createapikeys create was only for the headscale admin console and not really needed. next i edited the config.yaml @/etc/headscale/config.yaml as per the instructions on headscale install guide i adjusted the following 2 lines at the top of the file to meet my needs:
server_url: http://<your.domian.here>:8080
# Address to listen to / bind to on the server
#
# For production:
# listen_addr: 0.0.0.0:8080
listen_addr: 0.0.0.0:8080these tell headscale where to listen and will indicate what domain name youll be authenticating from outside your lan like i need
also, i have an NPM+ proxy running in my proxmox that handles all the traffic in/out, so i did a quick A record for my domain and setup NPM to look there and forward to the 8080 port above and voila!
next i had to setup a user:
headscale users create <username>
headscale users list
headscale preauthkeys create -u 1the users list command just confirmed that i did it right, at one point i had 2 users and was going through the command with -h or –help to figure our right syntax and how to delete the accidental user i created. the headscale preauthkeys command you will want to use for each tailscale instance you are authenticating later btw.
now i had a user and a key so i set about logging into my tailscale lxc. i did the client setup as recommended for in proxmox community pages.
https://community-scripts.github.io/ProxmoxVE/scripts?id=add-tailscale-lxc
avoid doing the tailscale up command as thats where we need to add our data for the headscale user and token. my command looked like this:
tailscale up --login-server https://<your.domain.address> --accept-dns=false --authkey <yourauthkeyfromabove>if everything is good it will just return to prompt, and you can just use:
systemctl status tailscaled
to check login info and see that things are running ok. the next tricky spot is to setup exit-node and advertise routes
tailscale set --advertise-exit-node
tailscale set --advertise-routes=192.168.100.0/24set your routes to you LAN 192.168.xxx.0/24
now it’s gunnabe sitting and waiting confirmation on your heasdscale server side, so you need to look with the 1st command, you should see the 0.0.0.0:0 and the LAN route you set above, but nothing showing in the approved column. execute the second command and you should see the approved column filled.
headscale nodes approve-routes –identifier 2 –routes 0.0.0.0/0,192.168.50.0/24
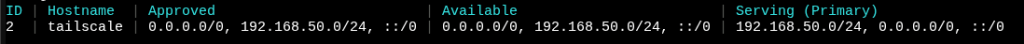
you should now have a fully setup exit node connected to your headscale server, within your local IP from which you can now connect to from the outside world after the following command on your tailscale node
tailscale set --exit-node <myexit>i was referencing and tweaking the commands i found here:
https://headscale.net/stable/ref/routes/?h=exit+node#exit-node
now that youve got that working you should be able to setup that network pretty easily from there on. for my laptop it was a simple set of commands:
create a second auth key as we did previously for your same user in the headscale server > this ensures that the user is tied to the same set of nodes > headscale and i presume tailscale would allow mulitple users to access the same nodes or have completely different nodes accessible and segregated user by user. i want the user to access the same nodes
sudo pacman -S tailscale
systemctl enable tailscaled
systemctl start tailscalednow instead of tailscale up, like we did with the exit node we want to login with the earlier command:
tailscale up --auth-key=<yourauthkeyfromabove> --exit-node=<hostname.exitnode> --login-server=https://<your.domain.name> --operator=joe --accept-routesnow with tailscale up enabled it connects to your exit-node, using the advertised routes and will allow you to access any IP in your local lan
for the phone: i downloaded tailscale from google play. now here you dont want to login to anything yet. create another authkey like above for the same user. i had to send via email to myself to be able to copy it into the app.
- hit the user menu in the upper right corner.
- click the accounts and then the 3 dot menu, click use an alternate server
- enter <your.domain.name> including https://
- go back to the same menu and click the use and auth key,
- add the authkey from above
- should see a blue check next to your user name you created
- now click connect, and once connected you can select the exit node <hostname>